Your passwords are up for grabs. Here's how security researchers find them.
Note: These methods do not work any longer due to the site referenced being taken down.
In January 2019, over 770 million password and username records were dumped onto the internet. The common security response to any new data dump is to use the very popular 'have i been pwned?' service. This awesome service can tell you if you're impacted by breaches like these, and will advise to change your password when it detects that an account linked to your e-mail address has leaked.
Criminals and security researchers might turn to this service to determine if a data dump should be scoured for credentials, but doesn't provide the actual credentials. We think that it's best to know the impact of your exposure by directly querying the sources criminals and security researches use. Knowing what the hackers know, or how common a password might be is really helpful in constructing useful mitigation solutions.
In the field of information security, there's always new and interesting tools popping up on the the internet, and we wanted to share a simple tool which was recently built by David Tavarez which can automate the retrieval of leaked credentials. This tool is named named pwndb.py and once installed, and you're connected to a TOR network (details in the link), you can query leaked data via cli. Let's check out the help;
$ python pwndb.py -h usage: pwndb.py [-h] [--target TARGET] [--list LIST] [--output OUTPUT] optional arguments: -h, --help show this help message and exit --target TARGET Target email/domain to search for leaks. --list LIST A list of emails in a file to search for leaks. --output OUTPUT Return results as json/txt --tor TOR Define port running tor
We can pass in a few arguments. Let's say we just want to search for any password associated with the commonly faked e-mail address, 123@abc.com. (Passwords are masked in this image)
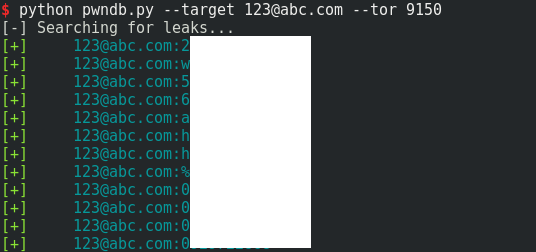
We can also search by domain. Let's say I want to review the passwords for all e-mail addresses associated with the abc.com domain. (Passwords are also masked in this image)

You can even pass through a list, especially useful when an organization might have several domains that need to be reviewed. You can check out helpful examples over at David's blog: https://davidtavarez.github.io
Check out your risk exposure by testing your own e-mail address. The hackers are, shouldn't you?
-Marbaṩ