CVE-2021-22521 - The ZEN of Privilege Escalation
DISCLAIMER: The content published here is the opinion of the person writing this, and that person alone.
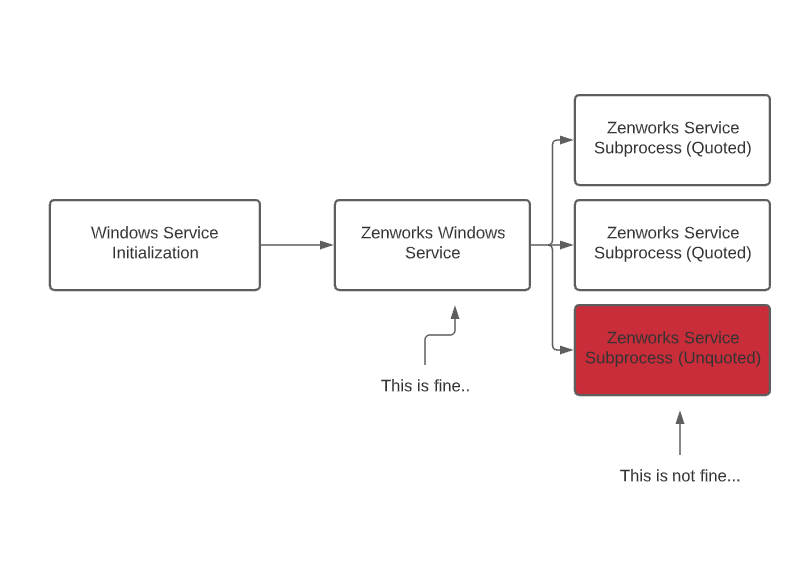
Way back in February I came across a vulnerability in a Novell product (now Microfocus) called ZENworks. Generally, it's a really simple vulnerability and something I think a majority of security folks could find with a tiny bit of effort. In a nutshell, it's a privilege escalation which could allow an attacker to gain system level permissions on an impacted host through, essentially unquoted service path issue.
First, if you don't know what an unquoted service path is, let's fill you in on that. When a Windows service is created, an executable path is always provided. Sometimes these paths can contains spaces, and if these paths are called by Windows with no quotes, it leads to a vulnerability known as an 'Unquoted Service Path'. This can allow the attacker to assume the role of a service. This works because when Windows creates new processes it will traverse the filesystem in a way which will automatically append an executable extension if a space is found in the path. So for example, if you had a program in C:\Ice Cream\Social Security Numbers\myservice.exe, and a service was called to open that path without quotes, Windows would try the following:
- First: It would attempt to open C:\Ice.exe
- Second: It would attempt to open C:\Ice Cream\Social.exe
- Third: It would attempt to open C:\Ice Cream\Social Security Numbers\myservice.exe
If you as a user have the ability to write content in the root of C:\, or in the C:\Ice Cream folder, you could add an executable which would subvert the execution of your service.
In our case, it wasn't the specific service that was vulnerable - it was the child processes in question here. Thinking back to our example, let's say our service was correctly called - but that service creates additional threads which Windows has to search for. Those threads are executed with the same permissions of the parent process. So it's important that those additional processes also must be called with quotations, or the child processes could be hijacked in the same way.
Sensibly, Microfocus was alerted and a critical system issue was opened in their ticketing system, stating that they thought it was serious. Here's what they said:

The organization I work for in my day job received a patch relatively quickly and Microfocus decided to leave other customers uninformed and without patches until the 21st of July, 2021. I've been keeping my eyes out for a vulnerability disclosure since there's been mostly radio silence from the vendor on if customers would be informed. I really wasn't planning on writing anything about this issue until my google alert on this product and came across the following forum post on their website.

I said to myself... cool, people got notified and are going to patch, great. It sucks that you need to specifically ask for a patch... but ok. What was really special is the what ZENworks support wrote in response to the question about the vulnerability disclosure.
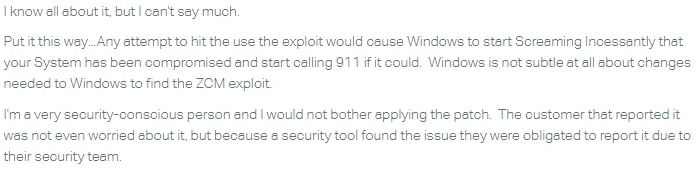 Wow.
Wow.

A few things to note, if you please, Microfocus support.
- If you in fact, knew all about it, you would be slightly more informed.
- Windows doesn't call 911 in this kind of event (or ever actually). In the proof of concept we sent to engineers, we gave your company instructions which do in fact create a noticeable impact which would alert users. The bad guys your company will attract will not announce themselves like this if they aim to exploit your software.
- Tools did not uncover this exploit, a manual review of the security of your software did, something I'd suggest investing in.
- If my day job org wasn't concerned, why'd they rush to patch? Maybe it had something to do with all of the supply chain attacks where management software (hello, Kaseya anyone?) are targeted by state actors and organized crime syndicates.
- All of this could have been known and your support agents could have been properly educated if you had bothered to reach out to and talk to the people who reported it.
End of day, the cherry on top of all of this for me is that this product and general platform is often used in organizations all over the world to manage security patches.
This likely means it's installed and distributed to EVERY COMPUTER on an impacted network to help mitigate security problems. Why in the world would Microfocus advise customers to not patch the product they sell to manage the installation and distribution of security patches?
But yeah, don't install it. Windows will call 911. Great advice.
- Microfocus KB7025205: Privileged Escalation Vulnerability (CVE-2021-22521) (microfocus.com)
- Registered CVE: CVE - CVE-2021-22521 (mitre.org)
- How to exploit this kind of vulnerability: Windows Privilege Escalation - Exploiting Unquoted Service Path Vulnerability (exploitblizzard.com)
-Marbaṩ